-
-
-
-
URL copied!
Here at GlobalLogic, we love working with HashiCorp tools. As a HashiCorp Hyper-Specialised Partner since 2016, we have been recognised for having deep expertise in deploying HashiCorp solutions that help customers embrace the cloud and accelerate their digital transformation journey.
One tool in particular is HashiCorp Sentinel, and today we’re going to take you through what Sentinel is and its integration with other HashiCorp products.
What is Sentinel?
Sentinel is an embeddable policy-as-code framework to enable fine-grained, logic-based policy decisions that can be extended to source external information to make decisions.
Sentinel allows customers to implement policy-as-code in the same way that Terraform implements infrastructure-as-code (IaC). It helps to solve the industry problem with regards to infrastructure standards when utilising IaC, ensuring consistency and compliance of developed configurations.
Why Sentinel?
Policy-as-code
Policy-as-code (PaC) refers to the ability to define organisational policies in areas such as security, compliance, or operational best practices as code. These policies can then be evaluated as part of an automated infrastructure provisioning workflow. Policies are encouraged to be stored as simple text files managed by a version control system. This provides you with the benefits of a modern VCS such as history, diffs, pull requests, and more.
Policy language
Sentinel policies are constructed using a high-level, purpose-built programming language. HashiCorp’s intent was for this language to be useable by those who may not come from a traditional development background. As a best practice, isolating policy writers (e.g. InfoSec) from those doing infrastructure deployments (e.g. Application Teams) is highly desirable. Sentinel policy repositories should exist separately from any infrastructure configurations.
Imports
Sentinel language includes the ability to employ reusable libraries through the use of imports. Anyone can write their own custom import. Imports are what enable Sentinel policies to do more than look at only local context for making policy decisions. They enable policy decision based on arbitrary external information. For example, a behaviour coming into a system can be allowed or denied based on information from a separate system where the two systems can be unaware of each other.
Enforcement levels
Sentinel’s enforcement level concept replaces the typical binary pass/fail nature of policy evaluation with three classification levels:
- Advisory: The policy is allowed to fail. However, a warning should be shown to the user or logged.
- Soft-Mandatory: The policy must pass unless an override is specified. The semantics of “override” are specific to each Sentinel-enabled application. The purpose of this level is to provide a level of privilege separation for a behaviour. Additionally, the override provides non-repudiation since at least the primary actor was explicitly overriding a failed policy.
- Hard-Mandatory: The policy must pass no matter what. The only way to override a hard mandatory policy is to explicitly remove the policy. Hard mandatory is the default enforcement level. It should be used in situations where an override is not possible.
Multi-cloud compatible
This ensures infrastructure changes are within business and regulatory policy on every infrastructure provider.
HashiCorp Sentinel integrations
Terraform Enterprise/Cloud
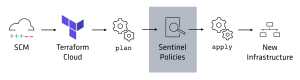
The Sentinel integration with Terraform runs within Terraform Enterprise/Cloud after a Terraform plan and before a Terraform apply. The policies have access to the created plan, the state at the time of the plan, and the configuration at the time of the plan.
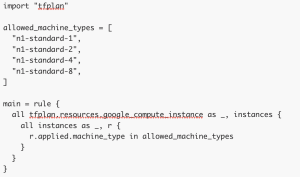
Policy example: Only allow GCP instance sizes smaller than n1-standard-16
Consul Enterprise
Consul Enterprise uses Sentinel to augment the built-in ACL system to provide advanced policy enforcement. Sentinel policies are applied during writes to the KV Store.
Sentinel policies have access to the key/value being written. They can be used to allow or deny the modification. The information that Sentinel policies have access to will expand over time.
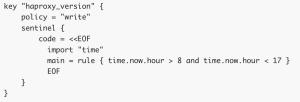
Policy example: The key haproxy version can only be updated during business hours.
Vault Enterprise
Vault Enterprise uses Sentinel to augment the built-in policy system to provide Role Governing Policies (RGPs) and Endpoint Governing Policies (EGPs) to enable complex, flexible policies across identities and endpoints.
Role Governing Policies (RGPs) are Sentinel policies that are tied to particular tokens, Identity entities, or Identity groups. They have access to a rich set of controls across various aspects of Vault. These are evaluated whenever a token they’re attached to is used.
Endpoint Governing Policies (EGPs) are Sentinel policies that are tied to particular paths instead of tokens. They have access to as much request information as possible, but they can take effect even on unauthenticated paths, such as login paths.
Sentinel can access properties of an incoming request and make a decision based on a certain set of conditions. Available properties include:
request – information about the request itself (path, operation type, parameters, etc.)
token – information about the token being used (creation time, attached policies, etc.)
identity – identity entities and all related data
mfa – information about successful MFA validations
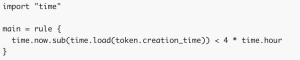
Policy example: disallow tokens generated over 4h ago.
Nomad Enterprise
Nomad Enterprise uses Sentinel to augment the built-in ACL system to provide advanced policy enforcement. Sentinel policies can currently execute on job submission (creation, update).
Sentinel policies have full access to the job structure. This allows the Sentinel policy to control behaviour based on any attribute within a job, such as the driver, resource requests, network configuration, volume configuration, and more. The information that Sentinel policies have access to will expand over time.
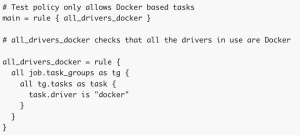
Policy example: Only allow Docker-based jobs.
Conclusion
HashiCorp Sentinel has all the benefits of encapsulation, maintainability, readability and extensibility that high-level programming languages offer, creating an attractive alternative to traditional, declarative security policy.
Sentinel is in the same class of tools as Open Policy Agent but is proprietary, closed-source and only works with HashiCorp products.
Looking to upskill your team with HashiCorp tools?
Learn to create consistent workflows that provision, secure, connect and run the infrastructure of your choice for any application. Each HashiCorp tool addresses a particular concern for the technical and organisational challenges of infrastructure automation – this means they can be adopted on at a time, or all together.
GlobalLogic offers a range of HashiCorp training packages, including Vault, Terraform, Consul and Nomad – enabling your team to integrate with the HashiCorp products and develop technical skills and go-to-market initiatives around DevOps principles, cloud technologies, and data centre management.
Reach out to Biagio Napoli for more information.
About the author:
My name is Wale and I’ve been working in the tech industry for eight years now. I’m currently working as a DevOps engineer with GlobalLogic and I’m passionate about all things Cloud, Python and HashiCorp products.
Sources
Download Sentinel by HashiCorp
Youtube – Introduction to Sentinel, HashiCorp Policy as Code Framework
Top Insights
Manchester City Scores Big with GlobalLogic
AI and MLBig Data & AnalyticsCloudDigital TransformationExperience DesignMobilitySecurityMediaTwitter users urged to trigger SARs against energy...
Big Data & AnalyticsDigital TransformationInnovationRetail After COVID-19: How Innovation is Powering the...
Digital TransformationInsightsConsumer and RetailTop Insights Categories

Let’s Work Together
Related Content
The GlobalLogic Academy Programme – a personal, introspective recollection
Ben Graham – Academy 2022 Graduate/Delivery Consultant I am currently in the DevOps capability for consulting and a recent graduate of the Academy 2022 programme which ran from September to December. I’d like to detail my thoughts on the process and share how my fellow graduates and I felt going on this journey. The GlobalLogic … Continue reading HashiCorp Sentinel: An introduction →
Learn More
Best practices for selecting a software engineering partner
More than ever, sports betting companies are under pressure to enhance customer value by tapping into the full potential of digital technology. However, traditional outsourcing models are not suited for digital engineering products. So understanding the difference between conventional outsourcing vendors and today’s software engineering partners is critical to success.
Learn More
Share this page:
-
-
-
-
URL copied!